Cryptowall takes over my computer
So….. Turns out the NHS, Fedex and a number of other companies and organisations have been hit by this same Ransomwear virus.
According to Avast, (who I use), there have been infections in 99 countries in the last 2 days.
Apparently, the NHS are still using windows XP on their computers. A 12 year old operating system.
Windows stopped patching XP on April 8, 2014.
That means it’s a sitting duck for systems using XP.
On my cloudflare account, most attacks come from XP computers, simply because they are so easy to commandeer and bend to the wills of evil hackers.
How to fight ransomwear?
If you, like I, did a search on this, “how to fight ransomwear, get rid of it from your computer”, it turns up a number of companies claiming to be able to ‘fix’ your system for exorbitant amounts of money.
I’ve done my own guide to removing ransomwear from your computer.
It works pretty well.
It worked when I got randsomwear, and you can find it here. My guide to removing ransomwear from your computer.
Below.
Article.
Cryptowall, ever heard of it? I hadn’t until tonight…
…. Watching Lost this evening… I went to open up VLC player, and I noticed that it was taking a long time to start-up.
Opening Process Explorer, I saw the SVChost, (a common windows task), in explorer.exe taking up around 4% of CPU.
Thought nothing of it. I know SVChost runs in the background carrying out important tasks for the operating system.
Watched Lost, (Series 4 Episode 8, ‘The shape of things to come’), as I finished, this PNG was displaying on Windows picture preview.
I’d not opened this file. It was telling me Cryptowall, whilst I was watching lost, had encrypted all the files on my computer using RSA-2048 encryption.
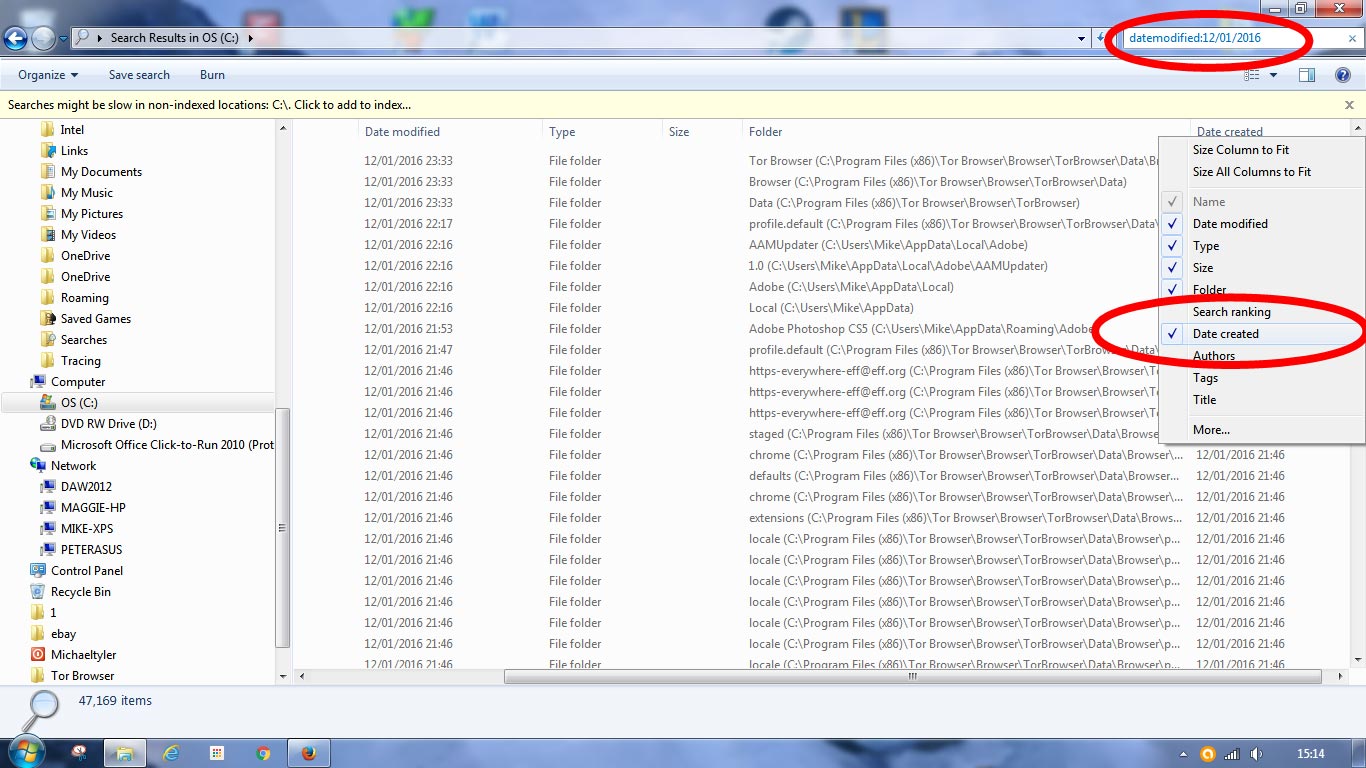
My Pictures Library now looks like this….

As you can see, they’re all encrypted.
I can’t access them. They’re no use to anyone in any way.
I re-booted. Nothing happened.
A ransom note from Cryptowall
[su_quote] Cannot you find the files you need? Is the content of the files that you have watched not readable?
It is normal because the files’ names, as well as the data in your files have been encrypted.
Congratulations!!!
You have become a part of large community #CryptoWall.
—
If you are reading this text that means that the software CryptoWall has removed from your computer.
—
What is encryption?
Encryption is a reversible transformation of information in order to conceal it from unauthorized persons but providing at the same time access to it for authorized users. To become an authorized user and make the process truly reversible i.e. to be able to decrypt your files you need to have a special private key.
In addition to the private key you need the decryption software with which you can decrypt your files and return everything in its place.
—
I almost understood but what do I have to do?
The first thing you should do is to read the instructions to the end.
Your files have been encrypted with the CryptoWall software; the instructions that you find in folders with encrypted files are not viruses, they are your helpers.
After reading this text 100% of people turn to a search engine with the word CryptoWall where you’ll find a lot of thoughts, advice and instructions.
Think logically – we are the ones who closed the lock on your files and we are the only ones who have this mysterious key to open them.
Any of your attempts to restore your files with the third-party tools can be fatal for encrypted files.
The fact is that changing data within the encrypted file (as 100% of software to restore files do this, except the special decryption software) you break damage to the file and it will be impossible to decrypt the file.
This is the same as to collect a mosaic when some mosaics items were lost, broken or not put in its place – the picture will not emerge, the software to restore the files will not be able to lay down the picture, and ruin it completely and irreversibly.
Using the software to restore files can ruin your files forever, only through your fault.
Remember that any intervention of the extraneous software to restore files encrypted with the Cryptowall software may be the point of no return.
—
In case if these simple rules are violated we will not able to help you, and we will not try because you have been warned.
For your attention the software to decrypt the files (as well as the private key that come fitted with it) is a paid product.
After purchasing the software package you can:
1. Decrypt all your files.
2. Work with your documents.
3. View your photos and other media content.
4. Continue your habitual and comfortable work at the computer.
If you are aware whole importance and criticality of the situation, then we suggest you go directly to your personal page where you will be given final instructions, as well as guarantees to restore your files.
There is a list of addresses below through which you can get on your personal page:
1.3wzn5p2yiumh7akj.waytopaytosystem.com/
2.3wzn5p2yiumh7akj.malkintop100.com/
3.3wzn5p2yiumh7akj.belladonnamonna.com/
4.3wzn5p2yiumh7akj.hiltonpaytoo.com/
What do you have to do with these addresses?
If you browse the instructions in TXT format (if you have instruction in HTML (the file that has an icon of your Internet browser) then for the sake of simplicity it is better to run it):
1. Look at the address number 1 (in this case it is 3wzn5p2yiumh7akj.waytopaytosystem.com/).
2. Select it with the mouse cursor holding the left mouse button and moving the cursor to the right.
3. Release the left mouse button and press the right one.
4. In the menu that appears select “Copy”.
5. Run your Internet browser (if you do not know what it is run the Internet Explorer).
6. Move the mouse cursor to the address bar of the browser (this is the place where the site address is written).
7. Click the right mouse button in the field where the site address is written.
8. In the menu that appears select the button “Insert”.
9. The address 3wzn5p2yiumh7akj.waytopaytosystem.com/must appear there.
9. Press ENTER.
10. The site must load; if it does not load, repeat the same instructions with the address number 2 and so on until the final address if falling.
If for some reason the site does not open check the connection to the Internet; if the site still does not open see the instructions on omitting the point about working with the addresses in the HTML and PNG instructions.
If you browse the instructions in HTML format:
1. Click the left mouse button on the address number 1 (in this case it is 3wzn5p2yiumh7akj.waytopaytosystem.com/).
2. In a new tab or window of your web browser the site must load; if it does not load, repeat the same instructions with the address number 2 and so on until the final address/.
If for some reason the site does not open check the connection to the Internet; if the site still does not open see the instructions on omitting the point about working with the addresses in the PNG instructions.
If you browse the instructions in PNG format:
1. We are very sorry but unfortunately your antivirus deleted instructions files in the TXT and HTML format for your comfortable work and most importantly for help to restore access to your files.
2. Try to enter the address of your page manually from a picture, good luck and patience for you.
Unfortunately, these sites are temporary because the antivirus companies are interested that you cannot restore your files but continue to buy their products.
Unlike them we are ready to help you always.
If the temporary sites are not available and you need our help:
1. Run your Internet browser (if you do not know what it is run the Internet Explorer).
2. Enter or copy the address into the address bar https://www.torproject.org/download/download-easy.html.en your browser and press ENTER.
3. Wait for the site loading
4. On the site you will be offered to download TorBrowser; download and run it, follow the installation instructions, wait until the installation is completed.
5. Run Tor-Browser.
6. Connect with the button Connect (if you use the English version).
7. After initialization a normal Internet browser window will be opened.
[su_highlight background=”#f3f82d”]8. Type or copy the address 3wzn5p2yiumh7akj.onion/ in this browser address bar.[/su_highlight]
9. If for some reason the site is not loading, wait a moment and try again.
If you have any problems during installation or operation of TorBrowser, please, visit www.youtube.com and type request in the search bar “install tor browser windows”. As a result you will see a training video on TorBrowser installation and operation.
If TOR address was unavailable for a long time (2-3 days) it means you were late; on average you have about 2 weeks after reading the instructions to restore your files.
—
Additional information:
Instructions to restore your files are only in those folders where you have encrypted files.
For your convenience the instructions are made in three file formats – html, txt, and png.
Unfortunately, antivirus companies cannot protect and moreover restore your files but they make things worse removing the instructions to restore encrypted files.
The instructions are not malwares; they have informative nature only, so any claims on the absence of any instruction files you can send to your antivirus company.
—
CryptoWall Project is not malicious and is not intended to harm a person and his/her information data.
The project is conducted for the sole purpose of instruction in the field of information security, as well as certification of antivirus products for their suitability for data protection.
Together we make the Internet a better and safer place.
———-
If you oversee this text in the Internet and understand that something is wrong with your files and you have no instructions to restore the files, contact your antivirus support.
———-
Remember that the worst has already happened and now the further life of your files depends directly on your determination and speed of your actions.[/su_quote]
My antivirus software prevented any of the conventional sites on the 1st four links from opening.
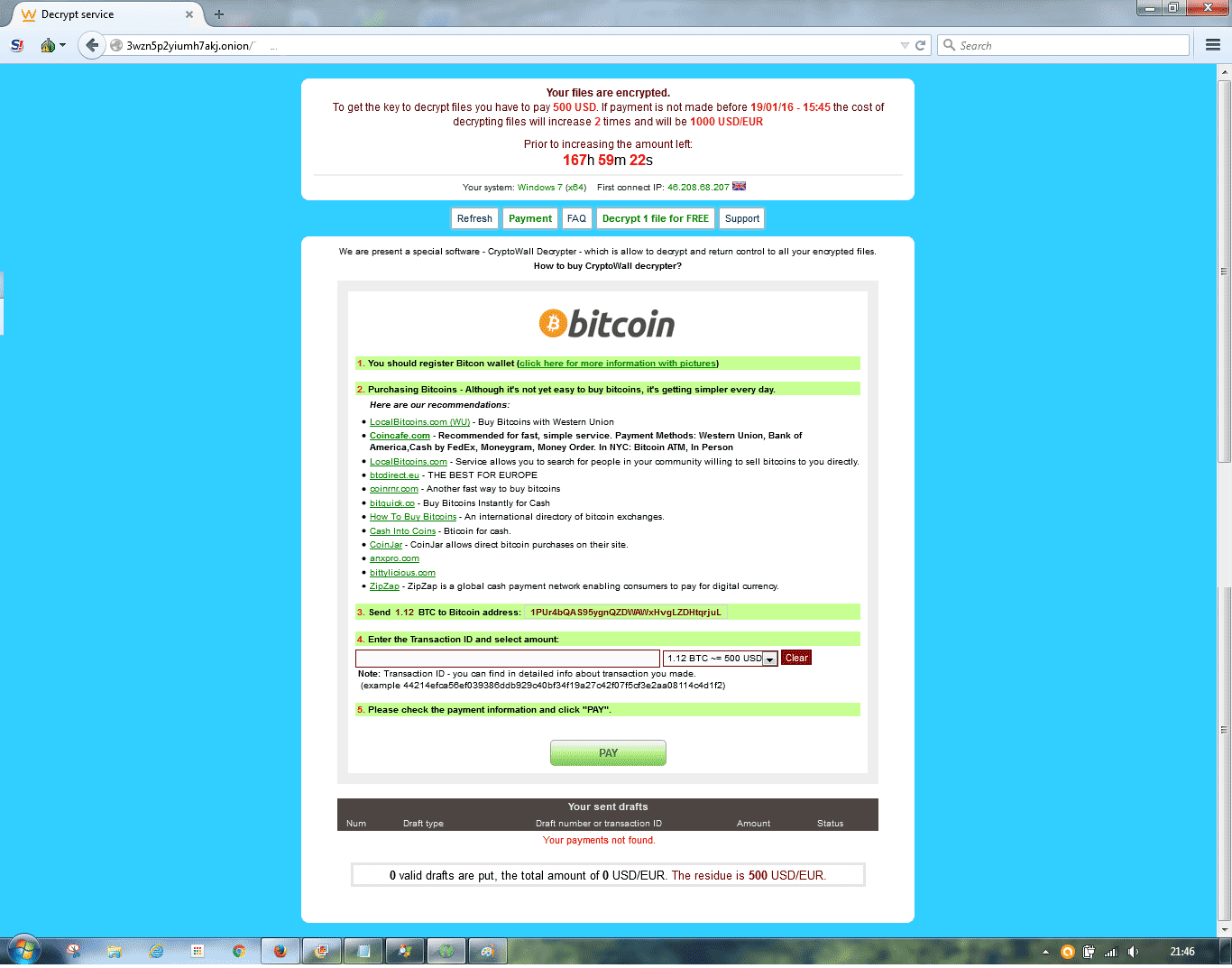
Cryptowall decrypt ransom demand
After some fishing around with the links, I got this one to open, in TOr Browser.
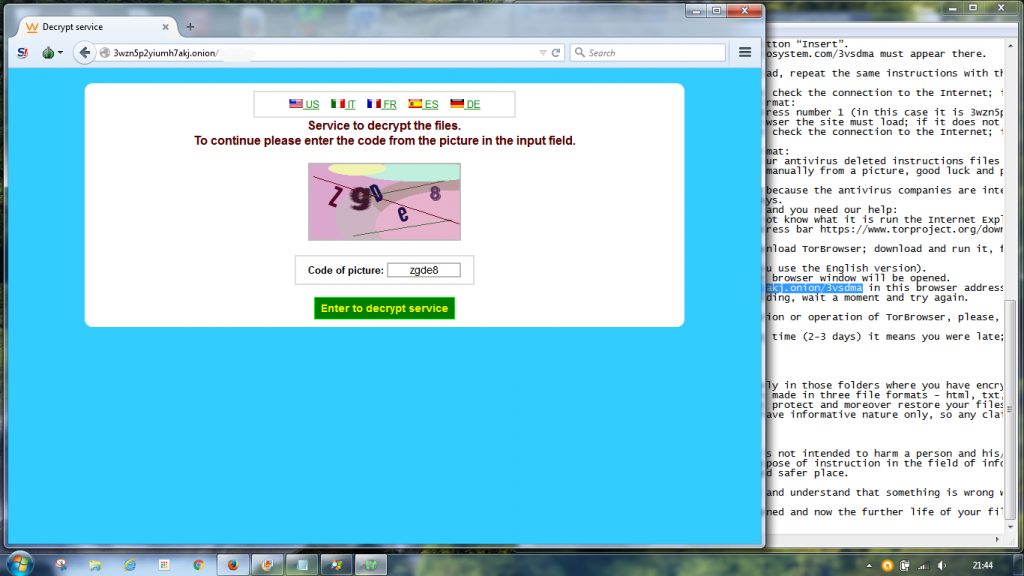
I had to enter a little catchpa.
Then
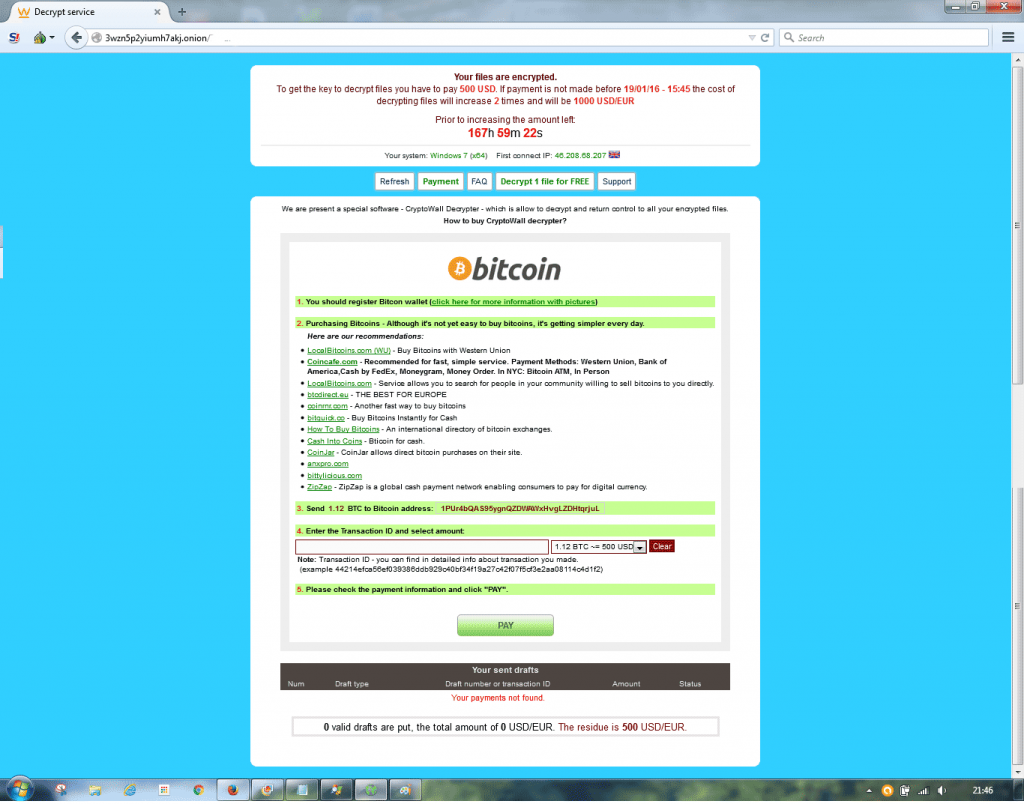
As you can see, they ransom demand is for $500 within 161 hours to get my files back.
Now, luckily, I backed all my documents up in April. And since then, I haven’t really been doing a whole lot…
Message to Cryptoguys….
So, if you guys are reading this, you’re going to have to suck my dick if you want that money…
How to remove Cryptowall and restore your files
For my next post I’ll be looking at how to remove the Cryptowall Virus and restore my computer after the Crytowall Virus.
So… thanks…. in a roundabout way, for encouraging me to write some decent new and sticky content…